How GitLab Helps Organizations Stay Ahead of Zero-Day Vulnerabilities

Zero-day vulnerabilities are among the most pressing challenges for cybersecurity professionals. Attackers exploit these flaws before a vendor can release a patch, leaving systems and data exposed and often making organizations susceptible to significant threats. Zero-day vulnerability protection is critical to safeguarding sensitive data, maintaining operational continuity, and ensuring customer trust.
GitLab, a leading DevOps platform, equips organizations with the security features they need to effectively manage zero-day vulnerability protection, continuously scan for vulnerabilities, and integrate security into every part of their development cycle.
By leveraging continuous integration and continuous deployment (CI/CD) security, automated vulnerability scanning, and real-time security monitoring and analytics, GitLab offers a comprehensive solution to mitigate zero-day vulnerabilities before they can cause damage.
In this post, we’ll explore how GitLab’s security tools empower organizations with zero-day vulnerability protection, focusing on proactive detection, real-time monitoring, and continuous vulnerability management.
What Are Zero-Day Vulnerabilities and Why Are They Dangerous?
A zero-day vulnerability refers to a flaw in software that is unknown to the vendor and, therefore, lacks a fix or patch. Cybercriminals can exploit this vulnerability before the vendor can respond, making it particularly dangerous.
Zero-day attacks can cause catastrophic damage, leading to data breaches, system outages, financial losses, and reputational harm. Since security patches are typically unavailable when a vulnerability is discovered, organizations are left exposed.
Given their severity, unlike traditional vulnerabilities, which can be managed through regular patching cycles, zero-day vulnerability protection requires early identification and rapid response. Without early detection and rapid mitigation, the risk of exploitation increases exponentially.
GitLab helps organizations mitigate these risks by integrating security into every CI/CD pipeline stage. This proactive approach ensures that vulnerabilities are caught before they enter production, reducing the likelihood of a successful zero-day attack.
Proactive Vulnerability Management: Key to Mitigating Zero-Day Risks
One of the most significant challenges in cybersecurity is transitioning from a reactive to a proactive security posture. Traditional security models that rely on reacting to discovered vulnerabilities can no longer keep up with the speed at which new vulnerabilities are introduced, especially with zero-day threats.
Proactive vulnerability management involves identifying, scanning, and mitigating security risks before they can be exploited. GitLab helps by offering a suite of tools that allow organizations to continuously scan code, identify vulnerabilities early, and apply patches as necessary. This approach reduces the window of opportunity for attackers to exploit zero-day vulnerabilities.
By integrating automated vulnerability scanning into the development process, GitLab ensures that vulnerabilities are identified at the earliest possible stage—while code is still being written. This is a far more effective approach than waiting for a vulnerability to be discovered in production.
GitLab Security Features: A Comprehensive Defense Against Zero-Day Vulnerabilities
GitLab offers a powerful suite of GitLab security features designed to help organizations avoid zero-day vulnerabilities. Below, we will compare GitLab’s integrated security tools with traditional vulnerability management processes to demonstrate the benefits of adopting GitLab for proactive, real-time protection.
Comparison of GitLab Security Features vs. Traditional Vulnerability Management
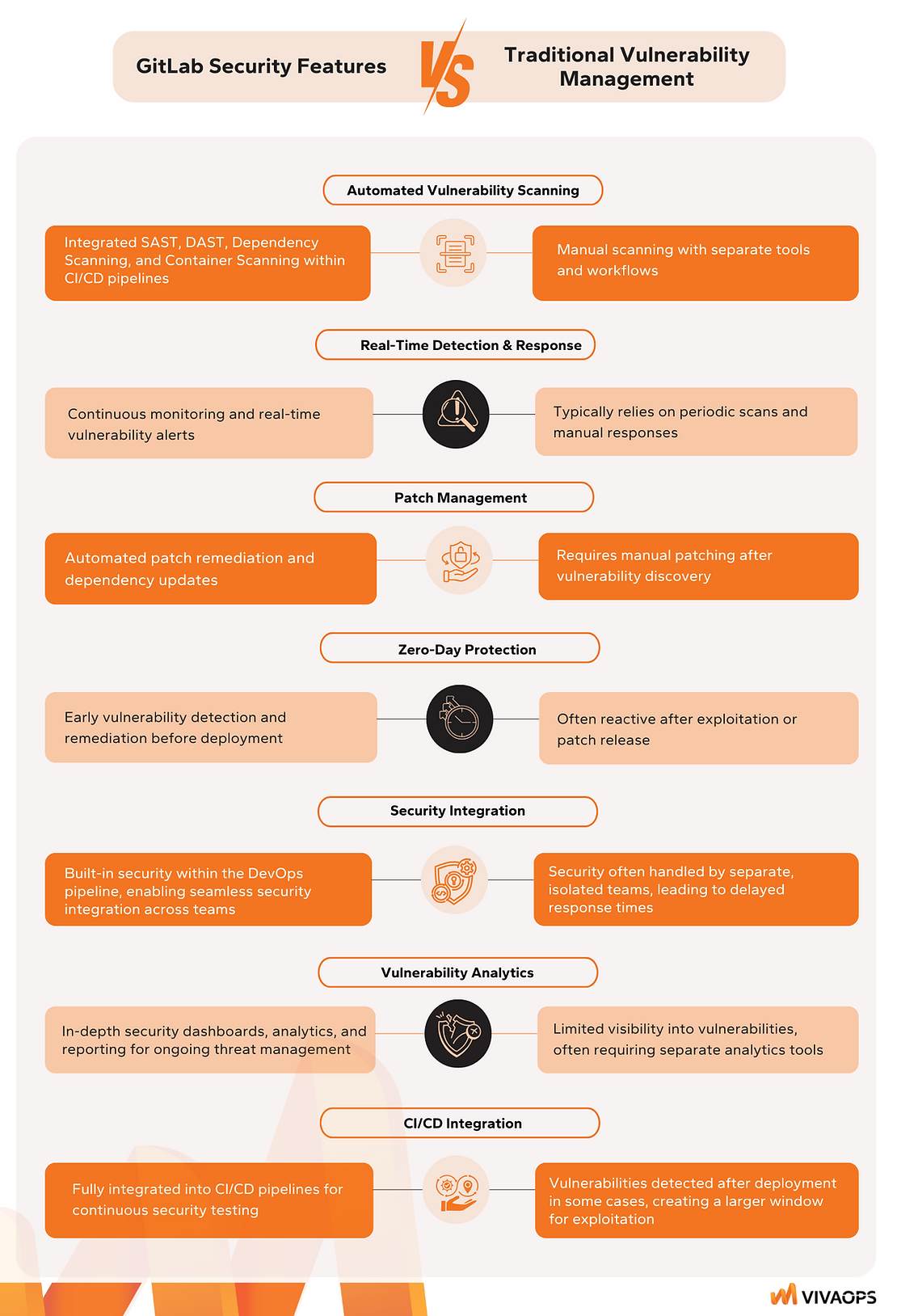
Explanation of Key Differences:
- Automated Vulnerability Scanning: GitLab integrates various security tools (SAST, DAST, dependency scanning, and container scanning) directly into the CI/CD pipeline, allowing vulnerabilities to be identified as early as the development stage. On the other hand, traditional vulnerability management typically requires separate manual tools to scan code, leading to slower identification and patching.
- Real-Time Detection & Response: GitLab provides continuous monitoring and real-time alerts for vulnerabilities, which allows teams to address any threats as they emerge quickly. In contrast, traditional methods often rely on periodic scanning, leaving a window of exposure for potential zero-day attacks.
- Patch Management: GitLab automatically suggests fixes and can even apply patches directly within the development pipeline, significantly reducing the time it takes to resolve vulnerabilities. In traditional systems, patch management is slower and requires manual intervention to update affected systems.
- Zero-Day Protection: GitLab’s proactive approach to security ensures that vulnerabilities are detected and remediated before they ever enter production. Traditional approaches, however, often only respond after a vulnerability has been exploited, leaving organizations at risk.
- Security Integration: GitLab offers a DevSecOps approach that integrates security throughout the development lifecycle. This integration ensures that security is considered at every stage and across all teams, reducing the time between identifying and fixing vulnerabilities. Traditional security models often isolate security into separate teams, leading to delays and miscommunication.
- Vulnerability Analytics: GitLab provides real-time analytics and dashboards for tracking vulnerabilities and assessing risks. Traditional tools often offer limited visibility into vulnerabilities, making it more difficult to prioritize and address them efficiently.
- CI/CD Integration: GitLab's key features are continuous integration and continuous deployment (CI/CD) security. It is fully integrated into the pipeline, providing continuous security testing from development to deployment. Traditional vulnerability management tools, however, are often disconnected from the CI/CD process, which can result in vulnerabilities being introduced during deployment.
Recommended Read: Enhancing Code Security and Compliance: GitLab’s Real-Time Insights
Real-World Case Studies: GitLab in Action
Several organizations have successfully used GitLab to prevent and mitigate the impact of zero-day vulnerabilities. Here are two examples:
Case Study 1: Financial Institution Securing Third-Party Libraries
A major financial institution integrated GitLab’s dependency scanning to secure its applications from vulnerabilities in third-party libraries. Automated vulnerability scanning of outdated or vulnerable dependencies equipped the institution to apply patches before attackers could exploit the vulnerabilities. This proactive approach to vulnerability management significantly reduced the risk of a zero-day breach and enhanced the institution’s overall security posture.
Case Study 2: SaaS Company Using SAST and DAST for Continuous Security
A SaaS company adopted GitLab’s SAST and DAST tools to scan their code and run applications for vulnerabilities continuously. Continuous integration and continuous deployment (CI/CD) security enabled the company to catch vulnerabilities early in the development process, preventing potential zero-day attacks from reaching production. This proactive approach saved the company from a costly and potentially disastrous security breach.
Both cases demonstrate the effectiveness of GitLab’s security tools in preventing zero-day vulnerabilities and maintaining a robust security posture.
Best Practices for Leveraging GitLab to Prevent Zero-Day Vulnerabilities
To maximize the effectiveness of GitLab’s security features, organizations should follow these best practices:
- Integrate Security into the CI/CD Pipeline: Ensure that SAST, DAST, and dependency scanning are integrated from the start of the development process.
- Automate Vulnerability Scanning: Leverage GitLab’s automated scanning to continuously monitor code and dependencies for vulnerabilities.
- Use Real-Time Security Dashboards: Use GitLab’s security monitoring dashboards to track vulnerabilities and take immediate action when threats are detected.
- Implement DevSecOps Best Practices: Ensure security is a shared responsibility across development, security, and operations teams, enabling faster responses to vulnerabilities.
By following these practices, security teams can dramatically reduce the risk of zero-day vulnerabilities and strengthen their security posture across the software development lifecycle.
Conclusion
Zero-day vulnerabilities are a significant and growing threat to organizations worldwide. However, with the right security tools, businesses can proactively manage these risks and stay one step ahead of cybercriminals. GitLab provides a comprehensive suite of security features, from SAST and DAST to automated patch management and dependency scanning, that are designed to detect and mitigate vulnerabilities before they reach production.
By integrating GitLab into your development workflows and adhering to DevSecOps best practices, you can ensure your organization is well-equipped to handle emerging threats and prevent zero-day vulnerabilities from causing damage.
.svg)
